
New evidence of Chinese tampering with Supermicro hardware ‘found in US telecoms company’
A security expert has provided evidence that reveals how China’s intelligence services had ordered subcontractors to plant malicious chips in server motherboards
The expert, Yossi Appleboum, provided documents, analysis and other evidence of the discovery that detailed how China’s intelligence services had ordered subcontractors to plant malicious chips in Supermicro server motherboards over a two-year period ending in 2015.
Appleboum previously worked in the technology unit of the Israeli Army Intelligence Corps and is now co-chief executive officer of Sepio Systems in Gaithersburg, Maryland. His firm specialises in hardware security and was hired to scan several large data centres belonging to the telecommunications company. The company is not being identified because of Appleboum’s nondisclosure agreement with the client.

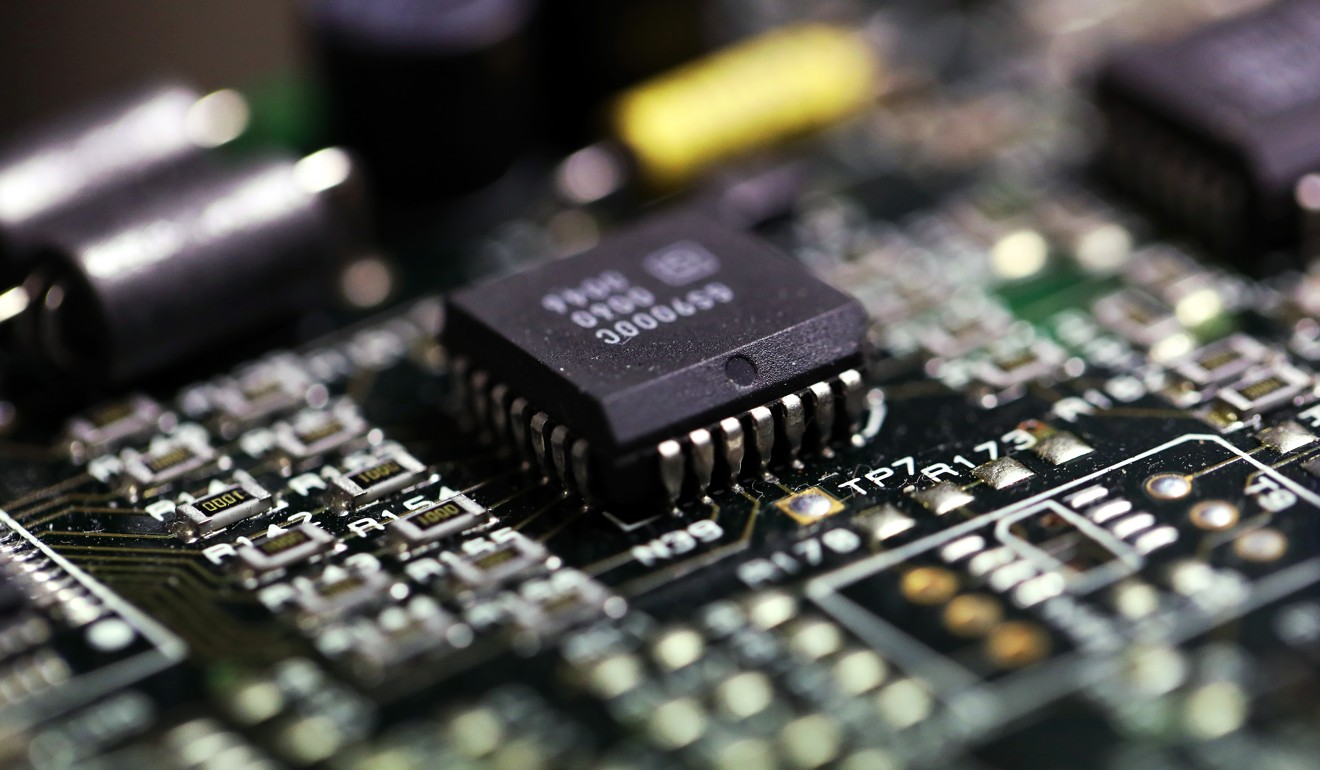
Unusual communications from a Supermicro server and a subsequent physical inspection revealed an implant built into the server’s Ethernet connector, a component that’s used to attach network cables to the computer, Appleboum said. He said he has seen similar manipulations of different vendors’ computer hardware made by contractors in China, not just products from Supermicro.
Appleboum said his concern was that there are countless points in the supply chain in China where manipulations could be introduced, and deducing them can in many cases be impossible. “That’s the problem with the Chinese supply chain,” he said.
Headquartered in San Jose, California, Supermicro was founded in 1993 by Taiwanese-American Charles Liang. The company gave this statement on Tuesday: “The security of our customers and the integrity of our products are core to our business and our company values.
“We take care to secure the integrity of our products throughout the manufacturing process, and supply chain security is an important topic of discussion for our industry.
“We still have no knowledge of any unauthorised components and have not been informed by any customer that such components have been found. We are dismayed that Bloomberg would give us only limited information, no documentation, and half a day to respond to these new allegations.”
Bloomberg News first contacted Supermicro for comment on this story on Monday morning Eastern time and gave the company 24 hours to respond.
Supermicro said after a Bloomberg BusinessWeek report last week that it “strongly refutes” reports that servers it sold to customers contained malicious microchips. China’s embassy in Washington did not return a request for comment on Monday.

In response to the earlier Bloomberg BusinessWeek investigation, China’s Ministry of Foreign Affairs didn’t directly address questions about the manipulation of Supermicro servers but said supply chain security was “an issue of common concern, and China is also a victim”.
The more recent manipulation is different from the one described in the report last week, but it shares key characteristics: They’re both designed to give attackers invisible access to data on a computer network in which the server is installed, and the alterations were found to have been made at the factory as the motherboard was being produced by a Supermicro subcontractor in China.
Based on his inspection of the device, Appleboum determined that the telecoms company’s server was modified at the factory where it was manufactured. He said that he was told by Western intelligence contacts that the device was made at a Supermicro subcontractor factory in Guangzhou, a port city in southeastern China.
Guangzhou is 90 miles upstream from Shenzhen, called the “Silicon Valley of Hardware”, and home to giants such as Tencent Holdings and Huawei Technologies.
The tampered hardware was found in a facility that had large numbers of Supermicro servers, and the telecommunications company’s technicians couldn’t answer what kind of data was pulsing through the infected one, said Appleboum, who accompanied them for a visual inspection of the machine.
It’s not clear if the telecommunications company contacted the FBI about the discovery. An FBI spokeswoman declined to comment on whether it was aware of the finding.
Representatives for AT&T and Verizon had no immediate comment on whether the malicious component was found in one of their servers. T-Mobile US and Sprint didn’t immediately respond to requests for comment.
Sepio Systems’ board includes Chairman Tamir Pardo, former director of the Israeli Mossad, the national defence agency of Israel, and its advisory board includes Robert Bigman, former chief information security officer of the US Central Intelligence Agency.
US communications networks are an important target of foreign intelligence agencies because data from millions of mobile phones, computers, and other devices pass through their systems. Hardware implants are key tools used to create covert openings into those networks, perform reconnaissance and hunt for corporate intellectual property or government secrets.
The manipulation of the Ethernet connector appeared to be similar to a method also used by the US National Security Agency, details of which were leaked in 2013.
In emails, Appleboum and his team refer to the implant as their “old friend” because he said they had previously seen several variations in investigations of hardware made by other companies manufacturing in China.

In Bloomberg Businessweek’s report, one official said investigators found that the Chinese infiltration through Supermicro reached almost 30 companies, including Amazon and Apple.
Both companies also disputed the findings. The US Department of Homeland Security said it had “no reason to doubt” the companies’ denials of Bloomberg Businessweek’s reporting.
People familiar with the federal investigation into the 2014-2015 attacks say that it is being led by the FBI’s cyber and counter-intelligence teams, and that the Homeland Security Department may not have been involved.
Counter-intelligence investigations are among the FBI’s most closely held, and few officials and agencies outside those units are briefed on the existence of those investigations.
Appleboum said that he had consulted intelligence agencies outside the US and that they told him they had been tracking the manipulation of Supermicro hardware, and the hardware of other companies, for some time.

